Il ransomware Memento blocca i file all’interno di un archivio protetto da password
per eludere la crittografia e chiede un riscatto di 1 milione di dollari in Bitcoin.
Sophos, leader globale nella sicurezza informatica di ultima generazione, ha pubblicato i dettagli relativi al funzionamento di Memento, un nuovo ransomware scritto in linguaggio Python.
Nella nuova ricerca “New Ransomware Actor Uses Password Protected Archives to Bypass Encryption Protection”, vengono descritte le caratteristiche di questo attacco che rinchiude i file all’interno di un archivio protetto da password quando non riesce a crittografare i dati che intende colpire.
“Gli attacchi ransomware effettuati con intervento umano sono raramente chiari e definiti nel mondo reale”, ha dichiarato Sean Gallagher, senior threat researcher di Sophos. “I cybercriminali sfruttano le opportunità quando si presentano e procedendo modificando tempestivamente le proprie tattiche e procedure di attacco.Se riescono a penetrare nella rete di una loro vittima, di certo non sono disposti a uscirne a mani vuote. L’attacco Memento costituisce un buon esempio di ciò, e serve a ricordarci di adottare soluzioni di sicurezza che attivino difese in profondità. Essere in grado di rilevare la presenza di ransomware e i tentativi di cifratura è essenziale, ma è altrettanto importante disporre di tecnologie di sicurezza capaci di allertare i responsabili IT in caso di altre attività inaspettate come il movimento laterale”.
Cronologia dell’attacco
I ricercatori Sophos sono convinti che i responsabili di Memento siano riusciti a entrare nella rete obiettivo dell’attacco a metà aprile 2021. Per far questo hanno sfruttato una vulnerabilità di VMware vSphere, un tool per la virtualizzazione del cloud computing rivolto a Internet, che ha permesso loro di penetrare all’interno di un server. Le prove forensi trovate dai ricercatori Sophos indicano che gli attaccanti hanno avviato l’intrusione principale agli inizi di maggio 2021.
Gli autori dell’attacco hanno usato i primi mesi a scopo di ricognizione e movimento laterale sfruttando Remote Desktop Protocol (RDP), lo scanner di rete NMAP, Advanced Port Scanner e il tool di tunneling Secure Shell (SSH) Plink per creare una connessione interattiva con il server violato. Gli attaccanti si sono avvalsi anche di mimikatz per raccogliere le credenziali degli account da utilizzare nelle fasi successive dell’attacco.
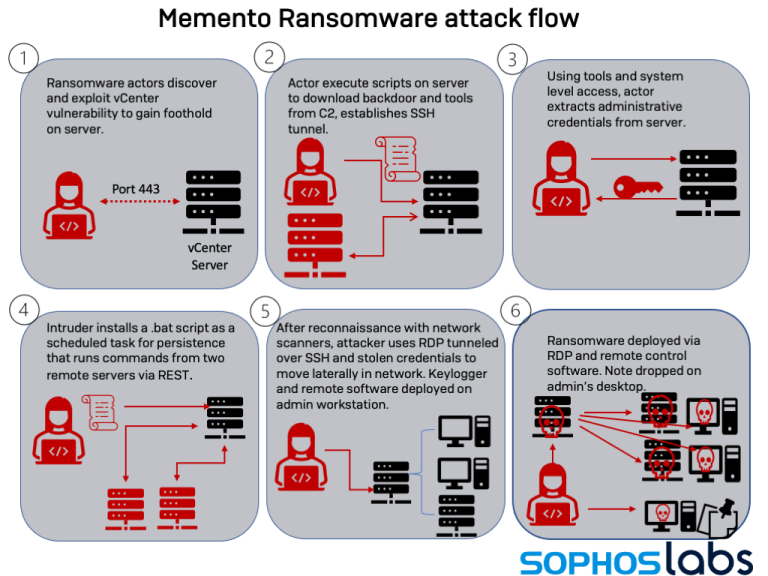
Secondo i ricercatori Sophos, il 20 ottobre 2021 gli autori di questo attacco hanno quindi usato un tool legittimo come WinRAR per effettuare la compressione di una serie di file esfiltrandoli quindi via RDP.
L’installazione del ransomware
Il deployment del ransomware è avvenuto il 23 ottobre 2021. I ricercatori Sophos hanno scoperto che chi attaccava ha provato inizialmente a crittografare i file, ma le misure di sicurezza in atto hanno impedito tale tentativo. I cybercriminali hanno quindi cambiato tattica, modificando e reinstallando il ransomware. Hanno copiato i file non cifrati in archivi protetti da password avvalendosi di una versione gratuita di WinRAR, prima di crittografarne la password e cancellare i file originali.
In seguito, hanno richiesto il versamento di un riscatto da 1 milione di dollari in Bitcoin per ripristinare i file. L’azienda colpita è stata fortunatamente in grado di recuperare i dati senza doversi rivolgere agli attaccanti.
Gli operatori ransomware sfruttano una vulnerabilità (CVE-2021-21971) nel client Web VMware vCenter Server per l’accesso iniziale alle reti delle vittime. Il problema è una vulnerabilità legata all’esecuzione di codice remoto non autenticato ed è valutato 9,8 sulla scala CVSS. Lo sfruttamento del problema consente a qualsiasi utente malintenzionato con accesso remoto alla porta TCP/IP 443 su un server vCenter aperto di eseguire comandi sul sistema operativo sottostante con privilegi di amministratore.
Una patch per questa vulnerabilità è stata rilasciata nel mese di febbraio di quest’anno, ma molte aziende non hanno corretto i propri sistemi.
Gli operatori di Memento hanno lanciato attacchi il mese scorso, sfruttando una vulnerabilità in vCenter per rubare credenziali amministrative, imporre la persistenza attraverso attività pianificate e quindi utilizzare RDP su SSH per navigare nella rete. Dopo la fase di ricognizione, i criminali hanno utilizzato WinRAR per creare un archivio di file rubati e esfiltrarli. Infine, hanno utilizzato l’utilità di pulizia dei dati BCWipe di Jetico per rimuovere eventuali tracce lasciate indietro, quindi hanno utilizzato una variante ransomware basata su Python per la crittografia AES.
Punti d’ingresso aperti hanno assecondato ulteriori attaccanti
Mentre gli autori di Memento si trovavano all’interno della rete colpita, altri cybercriminali sono entrati attraverso la medesima vulnerabilità sfruttando exploit simili. Ciascuno di essi ha installato sullo stesso server violato software per il mining di cryptovalute.. Un attaccante ha installato un cryptominer XMR il 18 maggio, mentre un altro ha installato un cryptominer XMRig l’8 settembre e, di nuovo, il 3 ottobre.
“Lo vediamo continuamente: quando le vulnerabilità accessibili da Internet diventano pubbliche e non vengono neutralizzate con le apposite patch, numerosi attaccanti corrono ad approfittarne. Più a lungo si aspetta per mitigarle, più attaccanti ne saranno attirati”, ha commentato Gallagher. “I cybercriminali eseguono costantemente la scansione di Internet alla ricerca di punti di ingresso vulnerabili, e di certo non si mettono in fila ad aspettare quando ne trovano una. Essere violati da più attaccanti non fa che moltiplicare i danni e i tempi di ripristino per le vittime, e rende anche più complicato per gli investigatori riuscire a far chiarezza e capire chi abbia fatto cosa, informazioni importanti per chi deve affrontare le minacce per aiutare le aziende a evitare ulteriori attacchi dello stesso genere”.
Consigli per la sicurezza
Sophos ritiene che questo incidente, nel quale più cybercriminali hanno violato un medesimo server privo di patch collegato a Internet, sottolinei l’importanza di applicare velocemente le patch e verificare la sicurezza del software di integratori, sviluppatori a contratto e service provider con cui si lavora.
Sophos consiglia inoltre le seguenti best practice generali per aiutare a difendersi da ransomware e relativi cyberattacchi:
A livello strategico
- Dispiegare una protezione a strati. Poiché gli attacchi ransomware iniziano sempre più spesso a comportare estorsioni, i backup rimangono necessari ma sono insufficienti. È più importante che mai tenere alla larga gli avversari o intercettarli rapidamente prima che possano provocare danni. Una protezione stratificata blocca e rileva gli attaccanti su più punti possibili all’interno di un ambiente
- Combinare esperti in carne e ossa con tecnologia anti-ransomware. Il segreto per fermare il ransomware risiede in una difesa in profondità che combini tecnologia anti-ransomware dedicata con attività specifiche condotte da esperti. La tecnologia fornisce la scala e l’automazione di cui un’azienda ha bisogno, mentre gli esperti in carne e ossa sono più adatti per accorgersi delle tattiche, tecniche e procedure che segnalano la presenza di un attaccante all’interno dell’ambiente. Se un’azienda non possiede le competenze al proprio interno può richiedere l’assistenza di specialisti in cybersicurezza
A livello tattico quotidiano
- Monitorare e rispondere agli allarmi. Assicurarsi che vi siano tool, processi e risorse (persone) disponibili per monitorare, investigare e rispondere alle minacce riscontrate nell’ambiente. Gli attaccanti sferrano spesso i loro attacchi fuori dagli orari di lavoro, nei week-end o durante le festività nel presupposto che non vi sia nessuno o quasi a controllare
- Definire e imporre l’uso di password forti. Le password forti sono una delle prime linee di difesa. Le password dovrebbero essere complesse o create apposta, e non essere mai riutilizzate. Per far questo con più facilità si può ricorrere a un password manager in grado di memorizzare le credenziali del personale
- Usare l’autenticazione multifattore (MFA). Anche le password forti possono essere violate. Qualsiasi forma di autenticazione multifattore è meglio che niente per proteggere l’accesso a risorse critiche come e-mail, tool per la gestione remota e asset di rete
- Bloccare i servizi accessibili. Effettuare scansioni della rete dall’esterno per identificare e chiudere le porte comunemente utilizzate da VNC, RDP o altri tool per l’accesso remoto. Se una macchina deve essere raggiungibile attraverso un tool per la gestione remota, fare in modo che quel tool risieda dietro a una VPN o a una soluzione per l’accesso di rete zero-trust che si avvalga di tecniche MFA come parte della procedura di login
- Ricorrere a segmentazione e zero-trust. Separare i server critici l’uno dall’altro e dalle workstation mettendoli all’interno di VLAN separate e andando in direzione di un modello di rete zero-trust
- Effettuare backup offline di informazioni e applicazioni. Mantenere i backup aggiornati, assicurarsi che siano recuperabili e conservarne una copia offline
- Inventariare asset ed account. La presenza nella rete di dispositivi sconosciuti, non protetti o privi di patch aumenta i rischi e crea una situazione nella quale le attività pericolose potrebbero passare inosservate. È essenziale disporre di un inventario aggiornato di tutto quel che è collegato. Usare scan di rete, tool IaaS e ispezioni fisiche per localizzare e catalogare i dispositivi, e installare software per la protezione degli endpoint su qualsiasi macchina priva di protezione
- Accertarsi che i prodotti per la sicurezza siano configurati correttamente. Sono vulnerabili anche i sistemi e i dispositivi solo parzialmente protetti. È importante assicurarsi che le soluzioni per la sicurezza siano configurate in modo appropriato; così come è importante verificare e, dove necessario, convalidare e aggiornare regolarmente le policy di sicurezza. Le funzionalità di sicurezza di nuova implementazione non sempre vengono attivate automaticamente. Non disabilitare la protezione anti-manomissione né creare ampie esclusioni dai controlli, dato che questo non farà che semplificare il lavoro degli attaccanti
- Verificare Active Directory (AD). Eseguire audit regolari su tutti gli account presenti in AD, accertandosi che nessuno di essi disponga di più accessi di quelli che gli sono effettivamente necessari. Disabilitare gli account dei dipendenti in uscita non appena lasciano l’azienda
- Applicare patch a tutto quanto. Mantenere aggiornati Windows e il resto dei sistemi operativi e del software. Questo significa anche verificare che le patch siano state installate correttamente e che siano presenti sui sistemi critici come i domain controller o le macchine collegate a Internet









